Docker Network: How to Create and Manage Docker Networks

Docker networking enables containers to communicate and share resources. Docker provides diverse networking solutions for containers. For example, there are the host, Bridge, and Macvlan network drivers. All of these network drivers are helpful in different use cases. Even the network driver that switches off all container network access is important for containers that need full isolation.
This article will teach you how to create a docker network using docker network create. You will also learn the five docker networking drivers that you have to master. In addition, you will learn how to inspect a Docker network.
#Prerequisites
You need to have installed Docker and have at least one container running that you will use to connect to a Docker network.
#What is a Docker network driver?
A Docker network driver is a component that enables and facilitates a container network. These network drivers configure network routes that enable network traffic between containers and external systems. Understanding what a Docker network driver is and how it works will help you know the best driver suitable for your application’s network needs.
You can use a network driver to instruct the container to communicate with internal containers only or cut off a container from the network grid. Docker network even goes further by giving a container the ability to be seen as a physical device.
The Docker network works by facilitating the host’s iptable rules to enable communication to your containers. Iptables is a utility program used for facilitating network packet rules. The Docker network drivers are made possible by adding iptables rules that filter how the network is distributed between containers. Docker configures iptables rules so you don’t have to manually configure iptables rules. Docker abstracts complex networking tasks so that users can only deal with low-level tasks that aren’t hard to configure.
Containers can communicate and identify each other in a network using IP addresses and names. Containers are not aware of the type of network they are assigned; they can only identify network interfaces together with their IP address details. By default, container network ports are not exposed; you have to expose them using the --publish flag. Containers inherit the host’s DNS, to specify a new DNS use the --dns flag.
To provide network isolation, Docker uses network namespaces that segregate containers based on the network they have been assigned to. Docker's network is virtual since it abstracts the system network.
Below is a list of Docker network drivers and their explanations:
- Bridge driver: By default, Docker containers use the bridge driver. The bridge driver is also known as docker0. The bridge driver allocates IP addresses to isolated containers and enables them to communicate with other internal containers connected to the host’s network.
- None driver: This network driver enables full isolation as it disables all of the container’s network stack. The container won't be assigned any IP address. This is useful for containers that have to be inaccessible to the host and other containers. A container that has no traffic has less chance of being exploited during a data breach.
- Host driver: This network driver enables the container to use the host’s IP address and port. The host network driver is used when you have to execute tasks directly on the host because the host driver removes isolation between the container and host.
- Overlay driver: This network driver enables communication between two Docker daemons. Since overlay networks allow containers on different Docker hosts to communicate they are used for facilitating network traffic between Docker swarm clusters.
- Macvlan: This network driver is very different from other network drivers because it enables your container to be recognized as a physical device. The container will be given a MAC address that makes it appear as a physical device.
Ready to supercharge your Docker infrastructure? Scale effortlessly and enjoy flexible storage with Cherry Servers bare metal or virtual servers. Eliminate infrastructure headaches with free 24/7 technical support, pay-as-you-go pricing, and global availability.
#How to list available networks?
Before creating a Docker network it is important to list all of the available networks. Some network drivers only allow you to create a limited number of networks. Use the following command to get a list of all the available networks:
docker network ls
You will get the following output that lists all available networks:
NETWORK ID NAME DRIVER SCOPE
1a569f1d219a bridge bridge local
dd2ac7eacce5 host host local
5878e9ded97e none null local
#How to create a Docker network
The docker network command is used for managing Docker networks. A Docker network can be created using the docker network create command. You have to specify the network driver type using the --driver flag followed by the name of the network. Below is the structure of the command you should follow when creating a network:
docker network create --driver [driver type] [network name]
Below is an example that creates a network called “devicenetwork” which uses the Macvlan network driver:
docker network create --driver macvlan devicenetwork
To check if the network was created successfully, execute the docker network ls command that lists all available networks. You will get the following output that shows that the devicenetwork was created successfully:
#How to connect a container to a network
Since containers use the bridge network driver by default. You have to manually connect the new network to the container using the docker network connect command. The command takes the name of the network and the container’s ID you want to connect to the network. Below is an example:
docker network connect devicenetwork c02a1be30158
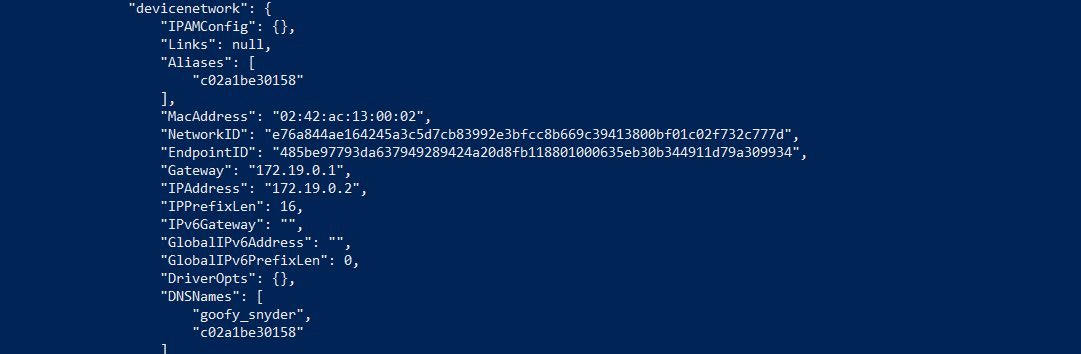
To check if the network driver has been connected successfully to the container, analyze it using the docker inspect command followed by the container’s ID which is c02a1be30158:
docker inspect c02a1be30158
You will get the following output that shows that the container is attached to the Macvlan network driver and it has been given a MacAddress that makes the container appear as a physical device:
If you no longer want a container to use the network. You can disconnect it using the following command:
docker network disconnect [network name] [container ID]
Also read: How to build a docker image from dockerfile
#Inspecting a Docker network
If a network is giving the container issues or not functioning as expected you should inspect its configurations. Inspecting the Docker networks can help you notice when the ingress and egress have been turned off. Below is an example that inspects the “devicenetwork” network.
docker network inspect devicenetwork
You will get the following output that gives comprehensive details about the network:
#Conclusion
In this guide, we have learned how to create a Docker network using the docker network create command. In addition, we have learned how to inspect container networks using the docker inspect command and how to list networks using the docker network ls command.
Found this guide helpful? Read more Docker guides on how to remove Docker images, how to set Docker environment variables and how to SSH into a Docker container.
Starting at just $3.24 / month, get virtual servers with top-tier performance.