Kubernetes Architecture Explained: Components & Workloads

A deep understanding of Kubernetes architecture differentiates a beginner from an expert debugger. Beyond Kubernetes' basic concepts, such as deployments and Pods, there are additional workload objects, such as CronJobs, and control plane components, like the cloud-controller-manager. Kubernetes surface concepts enable you to create and run deployments. However, you need a deeper knowledge of the Kubernetes architecture to fix issues such as network misconfigurations and persistent storage issues.
In this article, you will learn about Kubernetes architecture in detail. You will explore different concepts and mechanisms responsible for driving Kubernetes' underlying processes.
#The Kubernetes architecture explained
Without the implementation of a container orchestrator, many challenges will arise. Challenges such as manually scaling and managing containers in a distributed system where processes are dynamic. These challenges led to the creation of Kubernetes.
An open-source container orchestration platform that was designed to eliminate challenges experienced when scaling and managing microservices. Kubernetes eliminates these challenges by offering a centralized platform that gives insight and control over a large number of microservices.
Eleven years after its release, Kubernetes is still the best and undisputed tool for managing container applications and scaling applications during high-traffic and low-traffic periods. Kubernetes is deeply embedded in the DevOps workflow and is in high demand. This makes it worthwhile to invest your time and resources in learning Kubernetes thoroughly.
Below are prominent features that have made Kubernetes more appealing to DevOps engineers and CTOs.
- Scalability
- Resilience
- Portability
- Extensibility
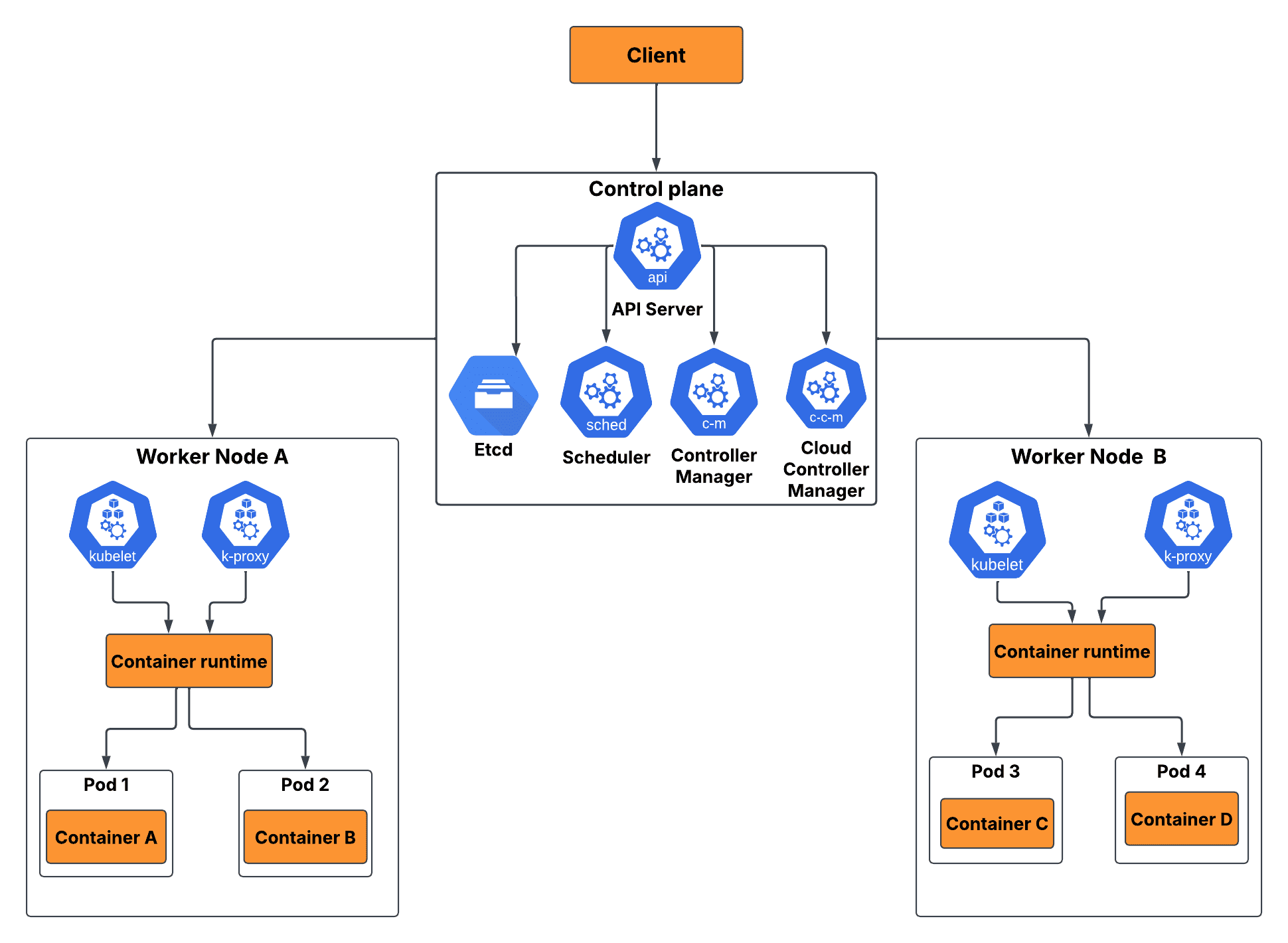
From a solid high-level view, Kubernetes is built on three broad categories: the control plane, workload objects, and the worker nodes. Understanding these components is essential for grasping how Kubernetes functions. Below is the Kubernetes architecture diagram.
#1. Kubernetes primary workload objects
In Kubernetes, workloads are applications running inside a Pod. Workloads can be stateless, stateful, batch jobs, or custom applications. Kubernetes provides different workload resources to manage workloads efficiently. Here's a list of primary Kubernetes workload objects responsible for carrying and deploying your applications seamlessly:
-
Pods and ReplicaSets: Pods are lightweight and easy-to-deploy workload objects that carry one or more applications. Pods run applications to which they have been assigned. A Pod has its own IP address. Since Pods are designed to be ephemeral, their IP addresses change when they are recreated. A Pod also has its namespace and storage.
Since Pods are short-lived, they are replaced by a ReplicaSet controller whenever a Pod dies. A ReplicaSet controller ensures that there is always an optimum number of Pod replicas running. It also keeps count of all running Pods and maintains the desired Pod number. ReplicaSets are managed by deployments.
-
Deployments: Deployments handle all processes involved in making the application available for use. They control Pods and enable you to specify the state of your application. Deployments facilitate gradual application rollouts and rollbacks without downtime.
Beyond rollout and rollbacks, Deployments offer other important features, such as scaling and self-healing. Scaling allows you to easily increase or decrease the number of running Pods based on demand, ensuring your application can handle varying workloads. Self-healing ensures that your application remains available by automatically replacing any Pods that fail. In short, Deployments provide a robust and reliable way to manage the lifecycle of your applications in a Kubernetes cluster.
-
StatefulSets: State management is a huge topic in the world of distributed systems. Kubernetes is an excellent choice for deploying, scaling, and monitoring containerized applications. Once your application has reached a certain complexity, you will need to implement state management if you want to continue developing it without running into roadblocks.
StatefulSets provides each Pod with a unique identity and stable, persistent storage. This is crucial for applications where the order and consistency of data matter. Use StatefulSets when your application needs to remember information across Pod restarts or requires a predictable network identity.
-
DaemonSets: DaemonSets enable fault tolerance in Kubernetes by scheduling Pods on more than one node. This ensures that services can continue functioning if one Pod fails because of an unhealthy node. The other Pods running on working nodes will make the application services available. A multi-node setup makes it easier to scale the application as demand grows, allowing for a more flexible and resilient infrastructure.
-
Jobs and CronJobs: A Job is a workload object that ensures that one or a batch of Pods operate successfully until they finish their assigned task and get terminated. A cronJob is a scheduled job that runs at a specific time or interval. They are important for periodic tasks such as backup or resource cleaning.
Build and scale your self-managed Kubernetes clusters effortlessly with powerful Dedicated Servers — ideal for containerized workloads.
#2. The Control plane
The control plane acts as the brain of the Kubernetes cluster, managing all activities in the cluster. It ensures that the desired state of the system matches the actual state. Below are components used by the control plane to manage the desired state of the Kubernetes cluster.
1. Etcd
The etcd is a key-pair value record that stores the state and cluster configuration data in key pair values. Every change made by the API server is recorded by the etcd. This makes it the source of truth for the cluster's event states. The etcd is a critical component that has to be secured and backed up always. Any disruption to the etcd will cause cluster instability or even failure.
2. API server
The API server or Kube-api server is responsible for exposing the Kubernetes REST API to internal and external network components. It is the central part of the Kubernetes architecture that handles communication. It centralizes all operations, ensuring that every part of the cluster communicates in a standardized way. This makes the system both modular and secure.
Every command you execute on kubectl is submitted to the API server. The API server will then process and validate the request. It will also record the request on etcd as a cluster event. Clients such as kubectl and other systems use the API server to interact and gain access to the cluster.
3. Scheduler
The scheduler assigns new Pods to a node that has sufficient resources. The scheduler follows criteria that review the node’s state and factors such as:
- Policy constraints
- Sufficient CPU and memory
- Good health
A node has to be marked fit by the scheduler before it is assigned to a Pod. By doing so, the scheduler ensures that workloads are balanced and resources are used wisely.
4. Kube controller manager
The Kube controller manager facilitates a group of controllers that monitors and enforces policies on the cluster. Controllers regulate the state of the cluster and ensure all resources are working as expected. An example of a controller is a DaemonSet controller that ensures that a copy of a specific Pod runs on every node.
5. Cloud controller manager
Besides the kube controller manager, there is a cloud controller manager that monitors and facilitates the integration of cloud components with the Kubernetes cluster. Any change in underlying cloud nodes or resources will be controlled by the cloud controller manager.
#3. Kubernetes worker node components
Kubernetes nodes are physical or virtual machines that run and host Pods. Worker nodes receive instructions from the control plane. Worker nodes host the components necessary to run workloads such as the kubelet, the container runtime, and other components. Below are components of a worker node that execute instructions laid out by the control plane.
- Kubelet: The Kubelet serves as the control plane agent. It controls how containers operate and which container to operate at a specific time. The Kubelet is responsible for managing available resources on the node and ensuring that containers get sufficient resources. It also checks and communicates container health to the control plane. This enables the control plane to monitor the overall status and health of the entire cluster.
- kube-proxy: The kube-proxy is responsible for all networking processes on a worker node. It provides a network interface for components to communicate with each other. It handles service discovery and load balancing. In addition, it enforces and implements network rules defined through network policies. These network policies keep the cluster secure by filtering unwanted networks through rules.
- Container runtime: The container runtime executes and manages the container lifecycle. The container runtime receives instructions from the Kubelet regarding container creation, deletion, and image pulling from DockerHub. An example of container runtime software is the containerd and CRI-O. The container runtime implements resource isolation by segregating containers from each other and from the host system.
#Kubernetes architectural essentials: security, storage provision to workloads, and networking
Below is an overview of Kubernetes concepts and mechanisms that enforce security, communication, and storage provision throughout the Kubernetes cluster.
#Kubernetes security
Security in Kubernetes involves multiple layers to protect the cluster and its workloads. It covers authentication, authorization, and accounting through audit logging. Role-Based Access Control (RBAC) is commonly used to enforce permissions. Other aspects include securing communication between components, managing sensitive data via secrets, and implementing network policies to control traffic flow between Pods.
Each of these layers contributes to a comprehensive security model, ensuring that Kubernetes clusters are resilient against unauthorized access and potential security breaches.
#Storage orchestration
Kubernetes handles storage orchestration by abstracting storage resources so that applications can consume persistent storage without having to manage the underlying infrastructure. Persistent Volumes (PVs) and Persistent Volume Claims (PVCs) enable dynamic provisioning and management of storage.
PVs represent units of storage that have been provisioned in the cluster. Either manually by administrators or automatically through dynamic provisioning. By abstracting the physical storage from the Pods that use it, PVs enable a more flexible approach where the underlying storage details are managed independently of the application lifecycle.
PVCs allow users to specify their storage needs in terms of size, access modes, and performance requirements without needing to understand the details of the underlying storage infrastructure. When a PVC is created, Kubernetes automatically matches it with a suitable PV. If no existing PV meets the criteria, the system can provision a new volume that aligns with the PVC’s specifications.
#Networking in Kubernetes
Networking in Kubernetes is built on a flat network structure where every Pod is assigned a unique IP address. Services provide stable endpoints and load balancing to abstract pod IPs. Ingress controllers manage external access to services. Network policies allow administrators to specify which Pods can communicate with each other, ensuring that network traffic follows defined security rules.
Network policies are a Kubernetes feature that provides fine-grained control over how pods communicate with each other and with external endpoints. They essentially act as a firewall for your Pods, allowing you to define which traffic is allowed or denied. Network policies are a critical tool for securing Kubernetes clusters by defining which pods can communicate with each other and controlling the flow of network traffic based on clearly defined rules
#Conclusion
In this article, you have learned the main components of the Kubernetes architecture. In addition, you have learned Kubernetes concepts that keep Kubernetes safe and functioning. Kubernetes remains the industry standard container orchestrator because it gives you a vast architecture that enables you to scale and manage your containers the way you want.
The vast Kubernetes architecture needs to be implemented in an easy-to-configure and resource-efficient machine. Cherry Servers provides you with a wide array of bare metal solutions, such as instant servers and custom servers. Bare metals allow you to install Kubernetes on a machine, which gives you complete control over hardware and OS specifications. You can explore more about Cherry Servers' bare metal solutions by setting up your bare metal infrastructure today.
Starting at just $3.24 / month, get virtual servers with top-tier performance.